HackTheBox – Active Subdomain Enumeration
Some background information, feel free to skip: I’m relatively new to pentesting. I’ve spent my whole career on the blue side, mostly with SIEM technologies. But that’s boring! I want to HACK! So my employer paid for some training and set a goal to finish HackTheBox Bug Bounty course and all TryHackMe modules this year. So I’m documenting my progress, good or bad. Learning can be embarrassing sometimes, but no one can know everything 🙂
The Lesson
I actually ran into some trouble with this one, so let’s take a closer look.
This lesson is about subdomain enumeration, and the first topic is a DNS zone transfer. This is how secondary DNS servers get updated information from the primary DNS server. The zone transfer spills all the information that the DNS server has, which can include some sensitive information sometimes.
Challenges:
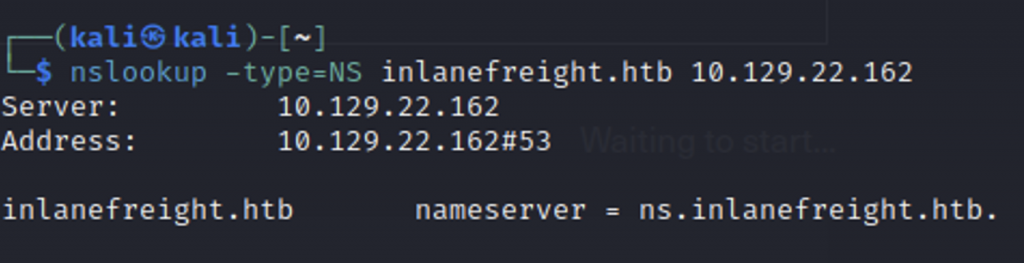
Submit the FQDN of the nameserver for the “inlanefreight.htb” domain as the server.
My problem with this one originally was I misunderstood the target (in my case, 10.129.22.162). The target IP address is the DNS server, not the name you’re trying to investigate! Once I ran my nslookup command correctly, I was able to easily find the FQDN of the nameserver.
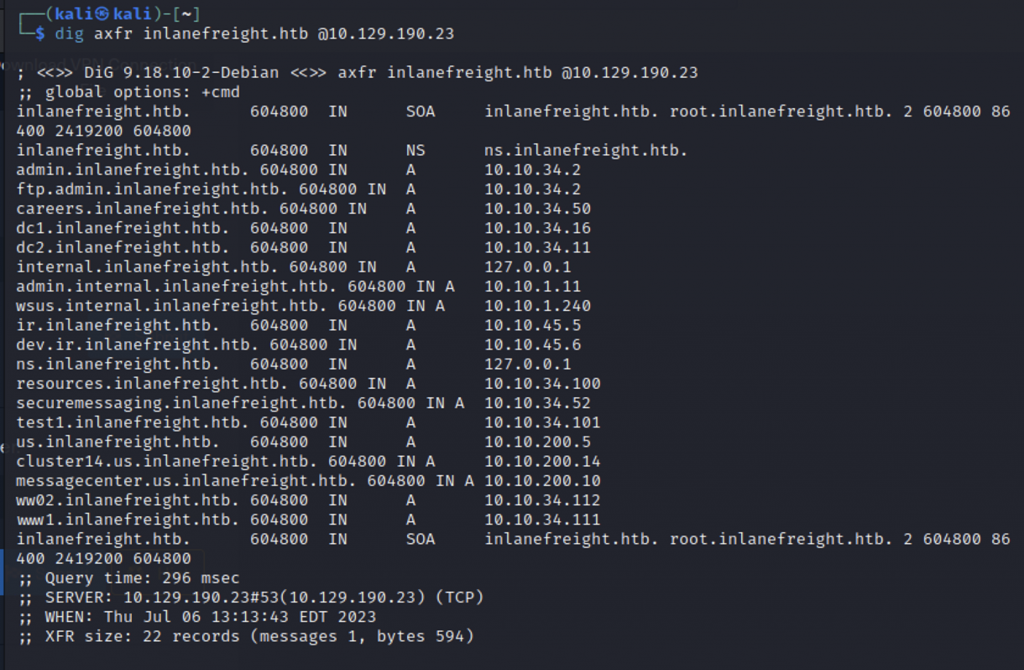
Identify how many zones exist on the target nameserver. Submit the number of found zones as the answer.
To be honest I had no idea how to do this. I guessed and I got the right answer. After I got the right answer, I did more research and added the IP address and inlanefreight.htb to my hosts file, then ran the zone transfer with dig. At this point it became clear that there are two zones inlanefreight.com and root.inlanefreight.com
Note: You’ll notice the DNS server IP address has changed in my screenshots. My machine timed out and I had to re-generate the target server. It’s not a trick 🙂
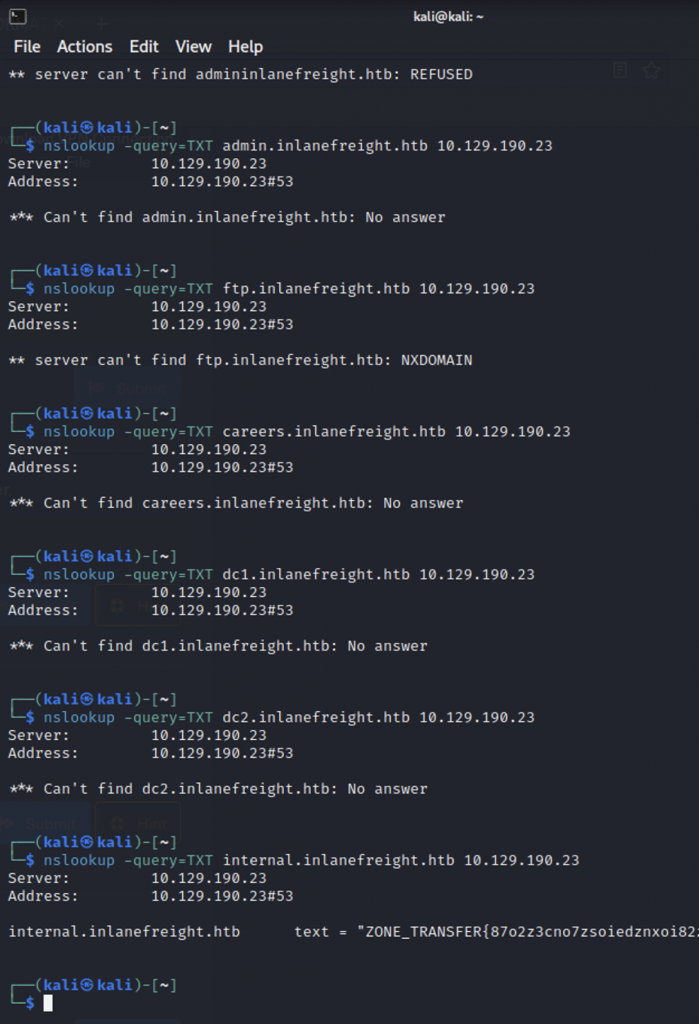
Find and submit the contents of the TXT record as the answer.
Is there a better way to do this? I’m sure there’s a better way to do this. I just brute-forced every single subdomain that I saw in the previous question until I saw a TXT answer back.
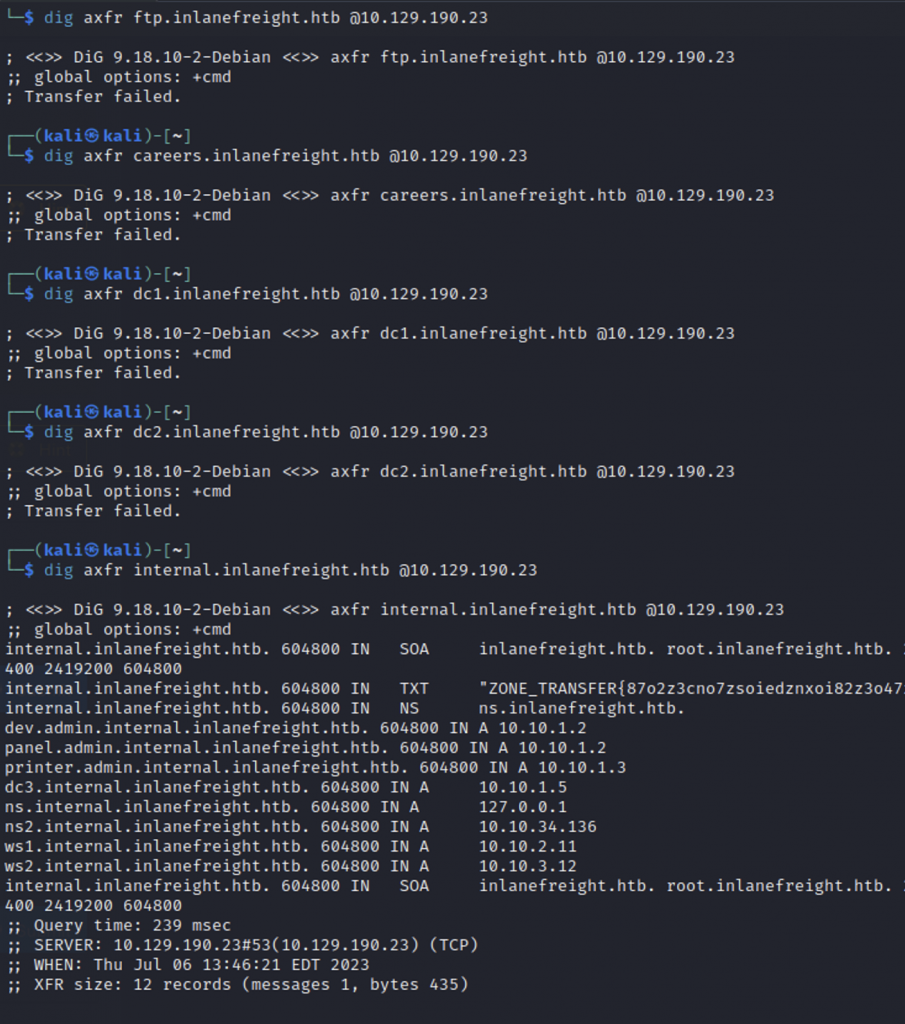
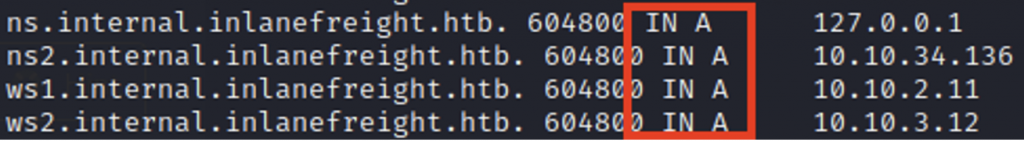
What is the FQDN of the IP address 10.10.34.136?
And
What FQDN is assigned to the IP address 10.10.1.5? Submit the FQDN as the answer.
There has to be a better way than just brute force. But I don’t know of one, so I use brute force. Just trying a zone transfer on every single subdomain I came across in the previous question. Eventually I found a subdomain that has zones in it as well.
Which IP address is assigned to the “us.inlanefreight.htb” subdomain. Submit the IP address as the answer.
The answer to this one is back in the first domain transfer question. Pretty easy if you’ve gotten this far.
Submit the number of all “A” records from all zones as the answer.
Again, if you’ve made it this far, you already have the answer. Just count all the A records for the zones you’ve enumerated to get here 😁
In Conclusion
I didn’t love this one. It took me several days to get through it because I felt it was vague and the lab did not really match the questions. Half the lesson was about Gobuster, which I did not use at all in this lab.
But also, I’ve discovered that I have a lot more to learn about DNS! In my research, I was recommended another HTB module, Footprinting. I’ll definitely have to dig into that one soon!
dig any internal.inlanefreight.htb @10.129.135.0 axfr
Will get you the answer without having to brute-force each domain. I stumbled upon this and figured I might share.
Nevermind. I am an idiot and didn’t realize I was already on that sub-domain.
Thanks for this, I couldn’t make sense of this module…was able to get through all of them after you pointed out that you could do the dig axfr on the subdomains that were originally found.